Access Windows based EC2 Instances securely using the Remote Desktop Gateway (RD Gateway) on AWS — by leveraging the AWS RD Gateway Quick Start
This is a small POC that I did to test the AWS Remote Desktop Gateway Quickstart https://docs.aws.amazon.com/quickstart/latest/rd-gateway/welcome.html The documentation of the quick start should be enough for hard-core Windows folks, but I am a Windows newbie or rather a lapsed Windows user;-) Hence, this will serve as a ready reference for future and current work. These steps would not have been possible without support from Ashita, from the AWS Premium Support team
When someone asks for a solution to access Windows-based instances using the Remote Desktop Protocol (RDP) on AWS, the most logical service to recommend is Amazon WorkSpaces — which is a managed, secure Desktop-as-a-Service (DaaS) solution from AWS — https://aws.amazon.com/workspaces/
But, there could be scenarios where Amazon Workspaces may not fit your requirements:
- Amazon WorkSpaces may not be available in your region, and you really need to spin up Workspaces ONLY from that region like may be due to an Compliance reasons. Please check for the latest service availability across AWS regions at https://aws.amazon.com/about-aws/global-infrastructure/regional-product-services/ . If its not available in your region, you can still use Workspaces from a different region, you can check the round trip time for WorkSpaces from different regions at https://clients.amazonworkspaces.com/Health.html
- You need a very specific version of Windows version. Amazon WorkSpaces offers Amazon Linux WorkSpaces built on Amazon Linux 2 LTS, or Windows 10 desktop experiences. The Windows 10 desktop experiences is powered by Windows Server 2016 (https://aws.amazon.com/workspaces/faqs/)
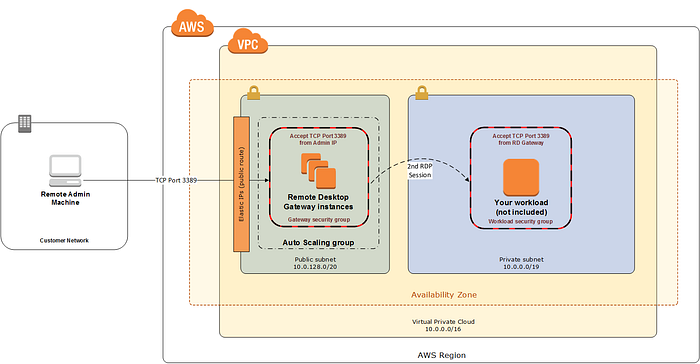
AWS quickstarts — https://aws.amazon.com/quickstart — help deploy popular technologies on AWS, based on AWS best practices for security and high availability .. Similarly to deploy a Remote Desktop Gateway on AWS, we have a Quickstart — https://docs.aws.amazon.com/quickstart/latest/rd-gateway/welcome.html
The requirement for the proof of concept was:
- Deploy the Remote Desktop (RD) Gateway securely in a VPC on AWS
- Deploy Windows EC2 Instances in private subnets with the same VPC
- Access the Windows instances via the RD gateway using an RDP client from my Mac laptop (this can also be a Windows laptop/desktop too).
Step 1: Deploying the RD Gateway Quick start
Run the Cloudfornation template for the quickstart from https://docs.aws.amazon.com/quickstart/latest/rd-gateway/deployment.html
The deployment gives several options, I selected the simplest one of a single RD Gateway server in a new VPC without domain join.
One gotcha, my mistake of course, when entering the parameter for the Admin password in the cloudformation template was to give a weak password, and the cloudformation failed a couple of times and the error thrown is not very descriptive in the console unless you go inside the cloudformation log in the Remote Gateway instance. Please make sure to follow the strong password guidelines — https://docs.aws.amazon.com/quickstart/latest/rd-gateway/step2.html#new
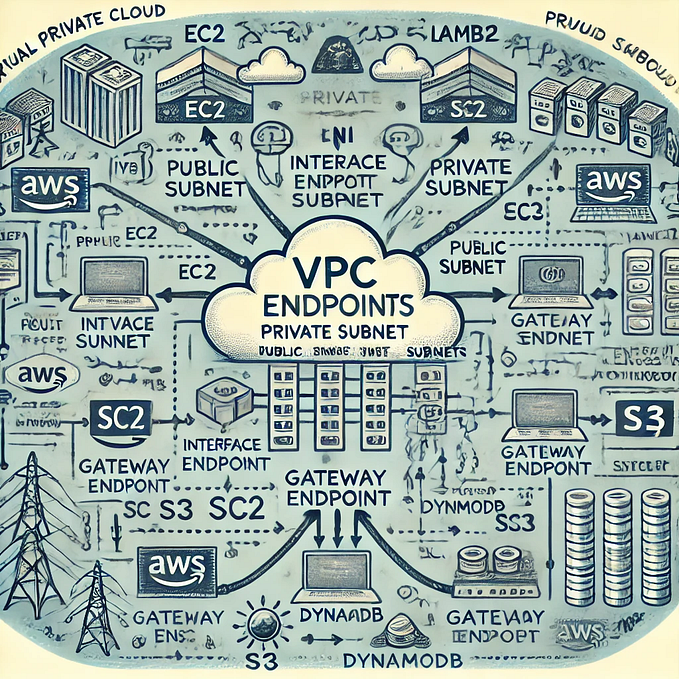
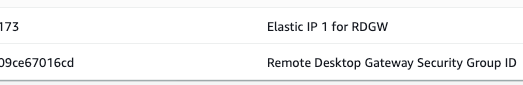
The cloudformation creates the following resources on AWS:
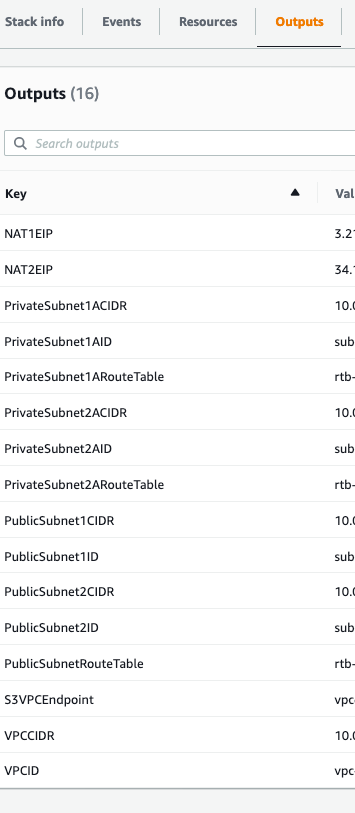
and the following information (from the cloudformation output) is required to connect to the RD Gateway
Step 2: Deploy Windows EC2 instances in the private subnet
The post deployment steps are given at https://docs.aws.amazon.com/quickstart/latest/rd-gateway/step3.html
I launched a few Windows EC2 instances in the same VPC that was created by the Quick start and in the private subnet.
There are a few things that we need to do:
- Security group settings for the Windows EC2 instances allowing traffic from the RD Gateway. You can allow ingress for the RD Desktop gateway security group ID that we obtained in the previous step.
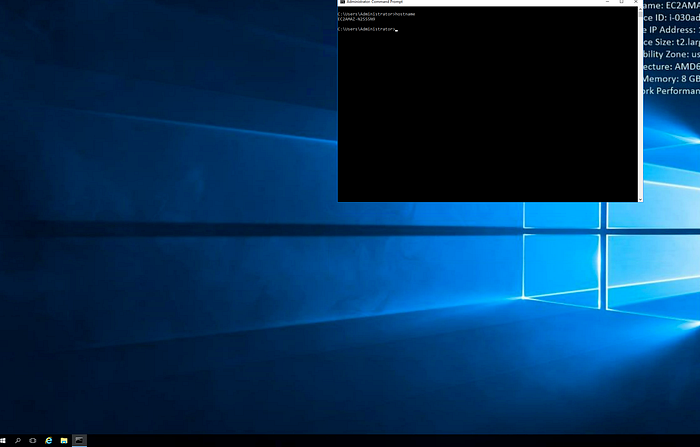
- We will need the private IP address and the host name of the Windows EC2 instances. The private IP address can be obtained from the AWS console and for the host name, you can use the following technique to get the hostname, without login to the instance ..
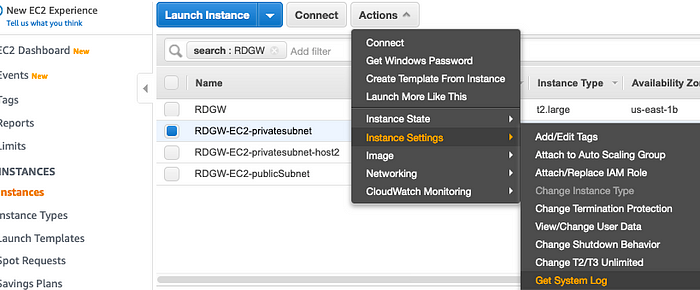

We will need to get the Windows Administrator passwords of the RD Gateway server, EC2 instances from the AWS EC2 console, keep them safe.
Follow the above steps to launch as many Instances, as you want in the private subnets.
Step 3: Access the Windows instances from Remote Desktop Client
From the post deployment steps are given at https://docs.aws.amazon.com/quickstart/latest/rd-gateway/step3.html
Installation of the RD Gateway server root certificate from the client machines will be required if your client (from where you will RDP to the RD gateway server) is Windows. I did not need to do this step, as I am using a Apple Mac Laptop.
Since, in the POC, I opted for a stand-alone deployment and not part of a domain join, we will need to hard code the following to ensure that the RD Gateway server can be resolved via a fully qualified domain name (FQDN). This has to be done in the hosts file in Mac at /etc/hosts (or Windows at C:\Windows\System32\Drivers\etc\hosts)
xx.xx.xx.xx EC2AMAZ-QLJQR5V.example.com
where EC2AMAZ-QLJQR5V.example.com is the FQDN of the gateway server and xx.xx.xx.xx is the public IP address of the RD Gateway server.
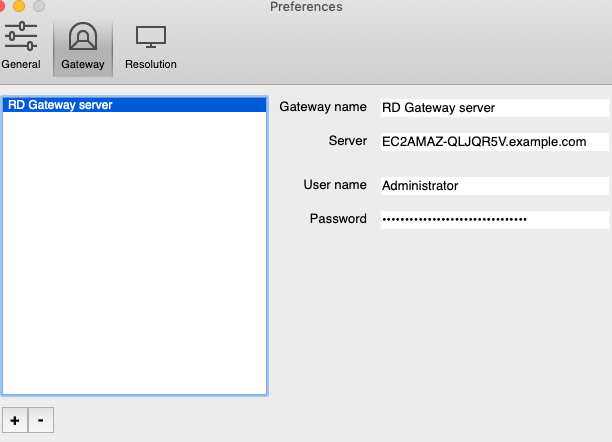
Finally, configure the Remote Desktop Client on my Mac laptop:
First the Gateway server settings:
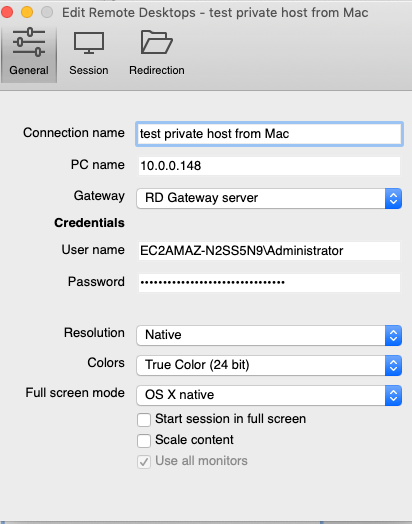
Next add an entry for the Windows EC2 instance running in the private subnet. Here the private EC2 instance IP address is 10.0.0.148 and host name is EC2AMAZ-N2SS5N9.
That’s it, voila, you can RDP into the private EC2 instance and start working :
Summary
We were able to use the AWS RD Gateway Quick Start (https://docs.aws.amazon.com/quickstart/latest/rd-gateway/welcome.htm) and setup the Remote Desktop Gateway server, and then connect to the Windows EC2 instances in a private subnet. The more easier and a managed way is to Amazon Workspaces, but this is also an alternate solution if you need one.
Hope this was useful.